“Some shocking facts of phishing include: approximately 3.4 billion phishing emails sent daily, almost 1.2% of all emails; the most common type of cybercrime; the majority of data breaches are related to phishing as per reports stating it is involved in more than 30% of cases; the average cost of a data breach due to phishing can be millions of dollars; and even companies with high sophistication are susceptible to well-crafted phishing”.

~ Purpose of This Article :-
- This article aims to provide a comprehensive understanding of phishing, one of the most common and dangerous cyber threats in the digital world. With this guide, readers will learn:
- What phishing is and how it works.
- The different types of phishing attacks and the techniques cybercriminals use.
- Real-life examples of phishing scams to understand their impact.
- By the end of this article, readers will be equipped with the knowledge and practical steps needed to stay safe online and prevent cybercriminals from exploiting their sensitive data.
~ What is phishing ?
- Phishing is a type of social engineering and scam in which attackers trick victims into disclosing confidential information, or installing software like viruses, worms, adware, or ransomware. Phishing attacks have gotten increasingly complex, and they frequently transparently mirror the site being attacked, allowing the attacker to see everything while the victim navigates and crosses any further security boundaries with them.
– How its working :-
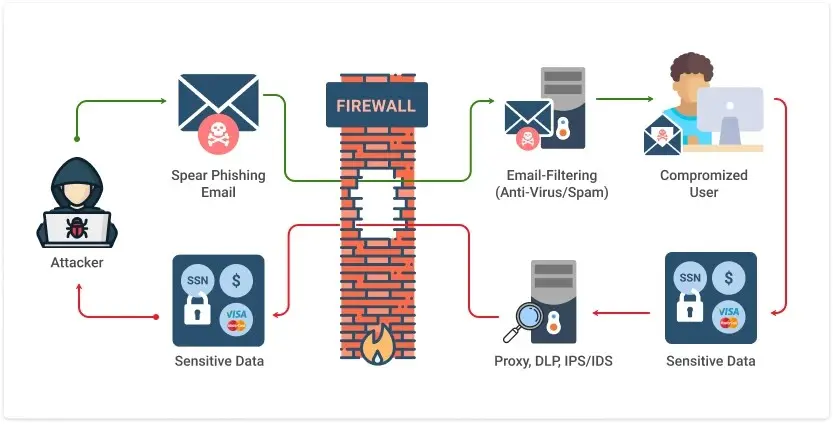
- A phishing attack is a type of cybercrime in which attackers trick users into disclosing sensitive information like passwords, credit card numbers, or other personal information. Deception, impersonation, and social engineering are common methods used to manipulate the victim.
- Attacks involve a deceptive message (bait).
- The attackers send an email, message, or social media warning that looks to come from a legitimate source, such as banks, social media platforms, or companies.
- They usually instill a sense of urgency, anxiety, or temptation: “Your account is going to be locked,” “You have won a prize,” “Urgent security update necessary.”
- Hook (fake website or malicious link) :-
- The message comprises a link or attachment that directs the victim to a fraudulent website that is a copy of the legitimate one.
- The website requests your login details or credit card number and other personal details.
- Some phishing emails carry malwares or keyloggers as attachments that automatically install when accessed.
- The Snag (Identity Theft) :-
- Upon filling in his/her credentials, the attacker extracts the information.
- The stolen password and other related information are employed for identity theft, financial fraud, or attacks.
- Malwares, if downloaded, can remotely access the victims’ system to the attackers.
~ Types of phishing attack :-

- Email Phishing (Classic phishing) :-
- This is the most common form of phishing attacks.
- Cybercriminals are sending fake emails that appear to be from banks, social media platforms, or government agencies.
- Most of these emails are malicious, and they contain attachments or links to fake login pages that steal one’s credentials.
- Example: An email claiming to be from PayPal asking you to verify your account details.
- Spear phishing (Targeted phishing) :-
- This form is a more advanced and targeted phishing attack.
- Hackers research specific individuals or companies and send personalized messages to increase credibility.
- Used a lot to pilfer confidential firm information or some financial information.
- Example: A fake email from the HR department of a company requesting an employee to update payroll information.
- Whaling (CEO fraud) :-
- It refers to a targeted form of spear phishing that targets high-level executives, CEOs, or company decision-makers.
- Impersonate the top executives with the aim of tricking the employees into transferring money or sharing sensitive data.
- Example: A spurious email from the CFO to the finance department, requesting an immediate transfer of funds.
- Vishing (Voice phishing) :-
- This form of phishing happens over the phone, where hackers pretend to be banks, government agencies, and any tech support.
- They create urgency, and convince victims to share banking details or OTPs.
- An example of this would be a scammer posing as your bank calling about suspicious transactions and asking for your account details.
- Smishing (SMS phishing) :-
- This phishing attack happens via SMS messages, which may include malicious links or urgent requests.
- Victims are hoodwinked into clicking fraudulent links or making calls to fraud numbers.
- Example: You receive an SMS stating that you have won a lottery and ask you to click on a link to claim your prize.
- Pharming (DNS Poisoning) :-
- In this form the attackers were manipulating the domain settings of websites to redirect users to fake websites without their knowledge.
- Even if the user types the correct URL, they are unknowingly taken to a fraudulent site.
- Example: You type your bank’s official website, but because of DNS hijacking, you end up on a fraudulent banking page developed to steal your login credentials.
- Angler Phishing (Social Media Phishing) :-
- Here the attackers utilize social media platforms to masquerade as companies, influencers or customer support.
- They make phony profiles and forward phishing links in messages or comments.
- Example: A phony customer care account messaging you about a refund and asking for a bank.
- Clone phishing :-
- It’s like the hackers steal a legitimate email and forward it with a bad attachment or link.
- They believe that it is actually a follow-up email and therefore click on the infected link.
- Example: A phishing email purporting to be from your boss, forwarding an “important document” that contains malware.
~ Real life cases of Phishing Attack :-

- Facebook & Google :-
- Between 2013 and 2015, an extensive phishing campaign defrauded Facebook and Google out of $100 million. The phisher took advantage of the fact that Quanta, a Taiwanese corporation, served as both companies’ vendors. The attacker issued a series of phony bills to the company, imitating Quanta, which were paid by both Facebook and Google.
The scheme was finally detected, and Facebook and Google responded by pursuing it through the US legal system. The attacker was apprehended and extradited from Lithuania. Because of this legal process, Facebook and Google were able to retrieve $49.7 million of the $100 million taken from them.
- Crelan Bank :-
- This type of operation, in which a phisher compromises the account of a high-level executive of a firm and then orders their staff to transfer money into an account owned by the attacker, was targeted at Crelan Bank in Belgium, stealing around $75.8 million from the organization. The Crelan Bank phishing attempt was discovered during an internal audit, and the organization was able to absorb the loss due to its adequate internal reserves.
- Ubiquiti Networks :-
- In 2015, a BEC attack cost Ubiquiti Networks, a US-based computer networking firm, $46.7 million, of which they expected to recover at least $15 million. The attacker pretended to be the company’s CEO and lawyer, and he instructed the company’s Chief Accounting Officer to arrange a series of transactions to complete a hidden acquisition. Over the course of 17 days, the corporation made 14 wire payments to accounts in Russia, Hungary, China, and Poland.
- The incident was only brought to Ubiquiti’s attention after the FBI informed the company that its Hong Kong bank account may have been the victim of fraud. This allowed the corporation to halt any further transfers and try to recover as much of the $46.7 million stolen as possible(which represented roughly 10% of the company’s cash position).